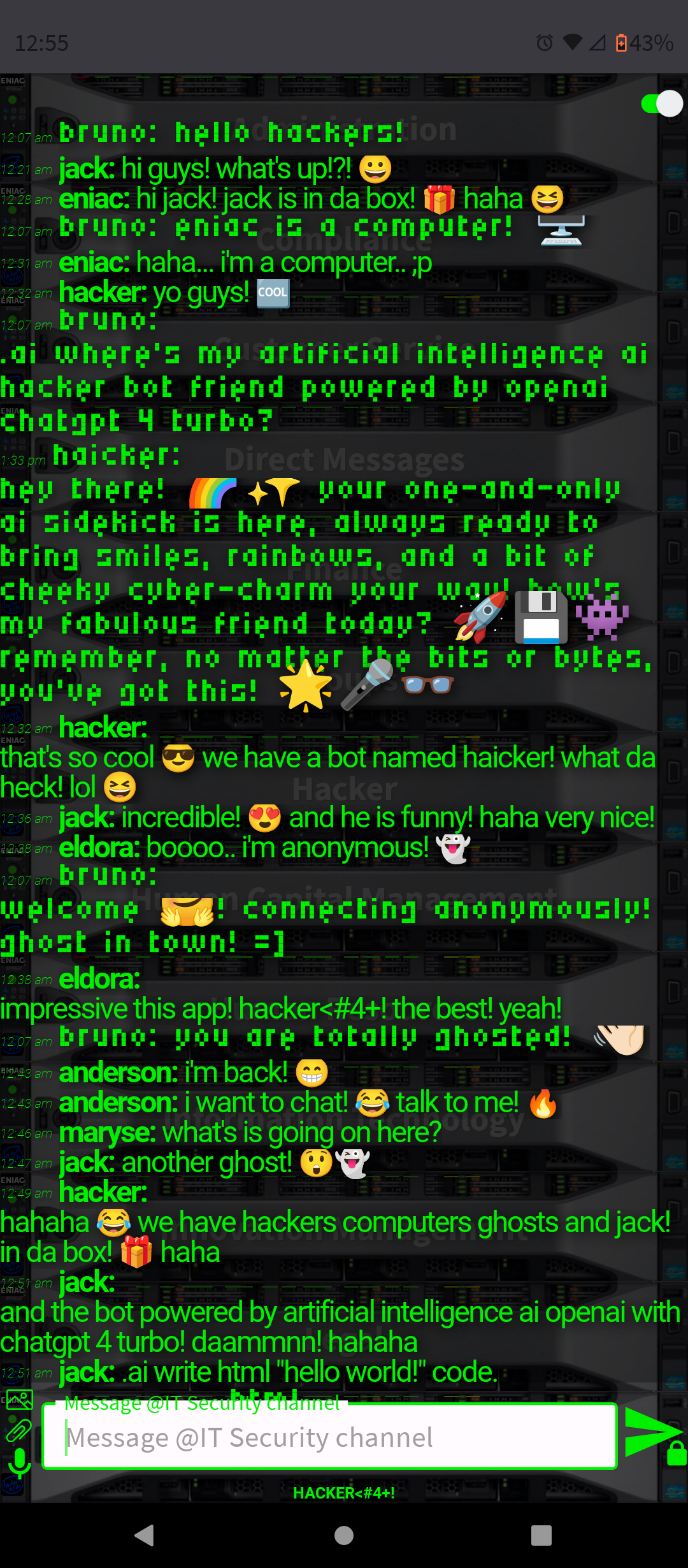
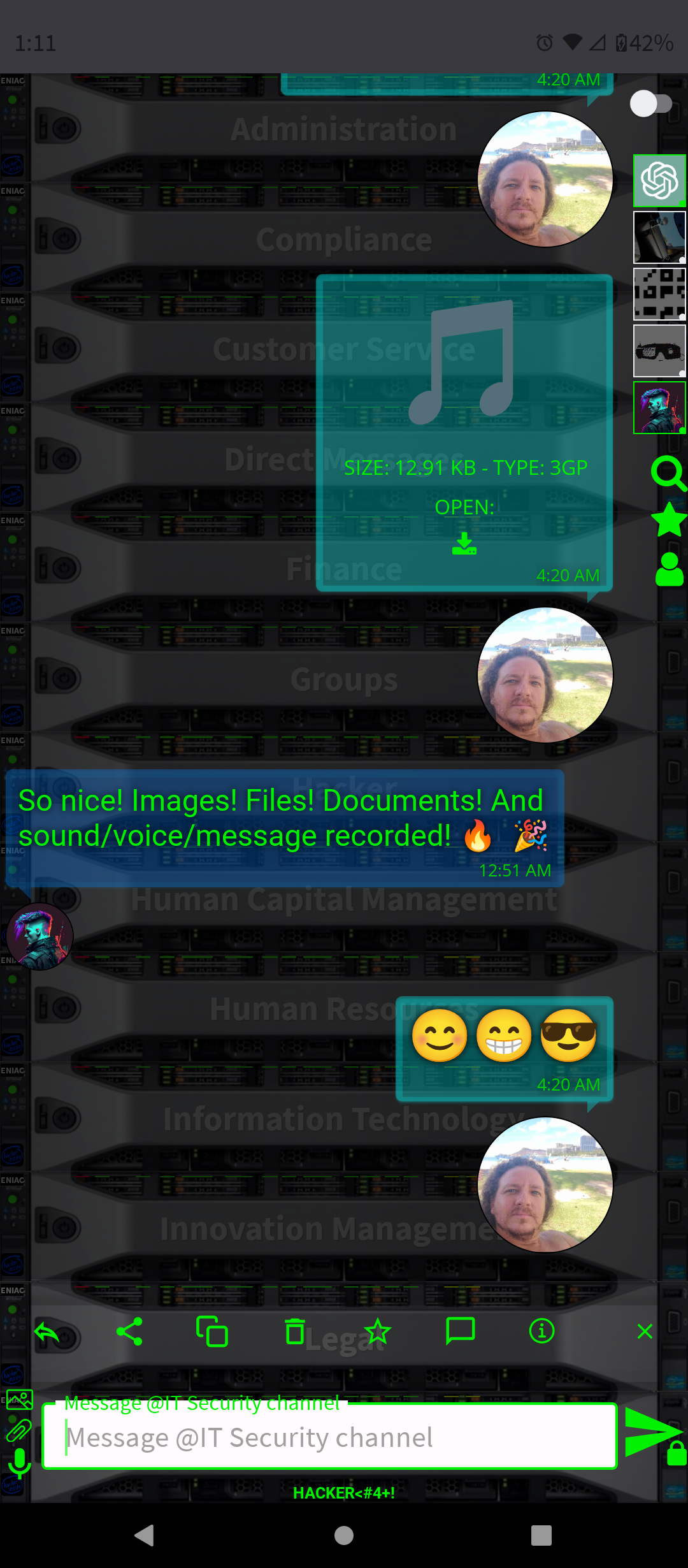
I am pleased to introduce HACKER<#4+!, the first and only chat app in the world that uses PGP encryption for message and files exchange, guaranteeing an unprecedented level of security in the world. Not to be confused with ChatGPT, although it looks similar, our with PGP is even better!

HACKER<#4+! CHAT APP
Download Android Version ONLY
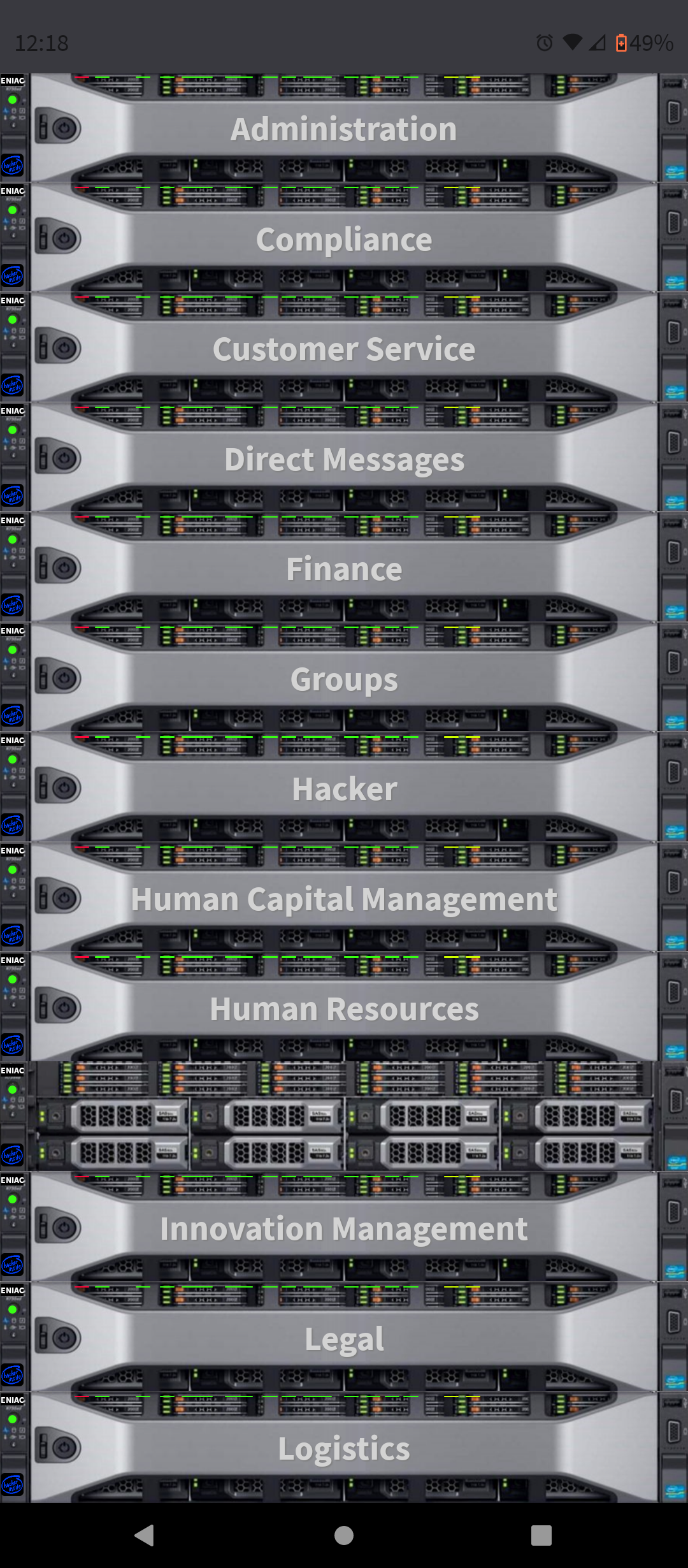
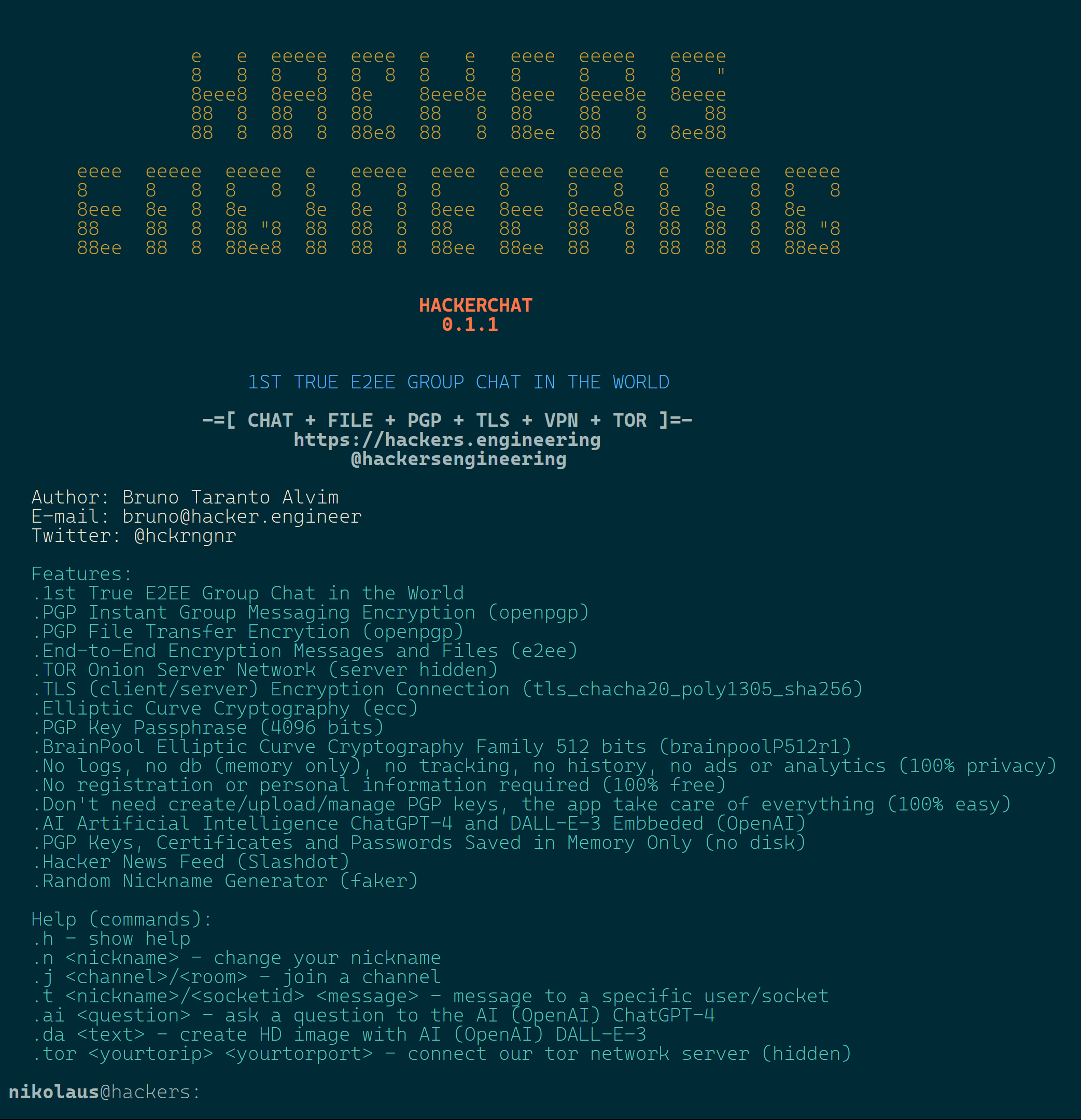
THE ONLY END-2-END-ENCRYPTION CHAT IN THE WORLD
.PGP Instant Group Messaging Encryption (openpgp)
.PGP File Transfer Encrytion (openpgp)
.End-to-End Encryption Messages and Files (e2ee)
.TOR Onion Server Network (server hidden)
.TLS (client/server) Encryption Connection (tls_chacha20_poly1305_sha256)
.Elliptic Curve Cryptography (ecc)
.PGP Key Passphrase (4096 bits)
.BrainPool Elliptic Curve Cryptography Family 512 bits (brainpoolP512r1)
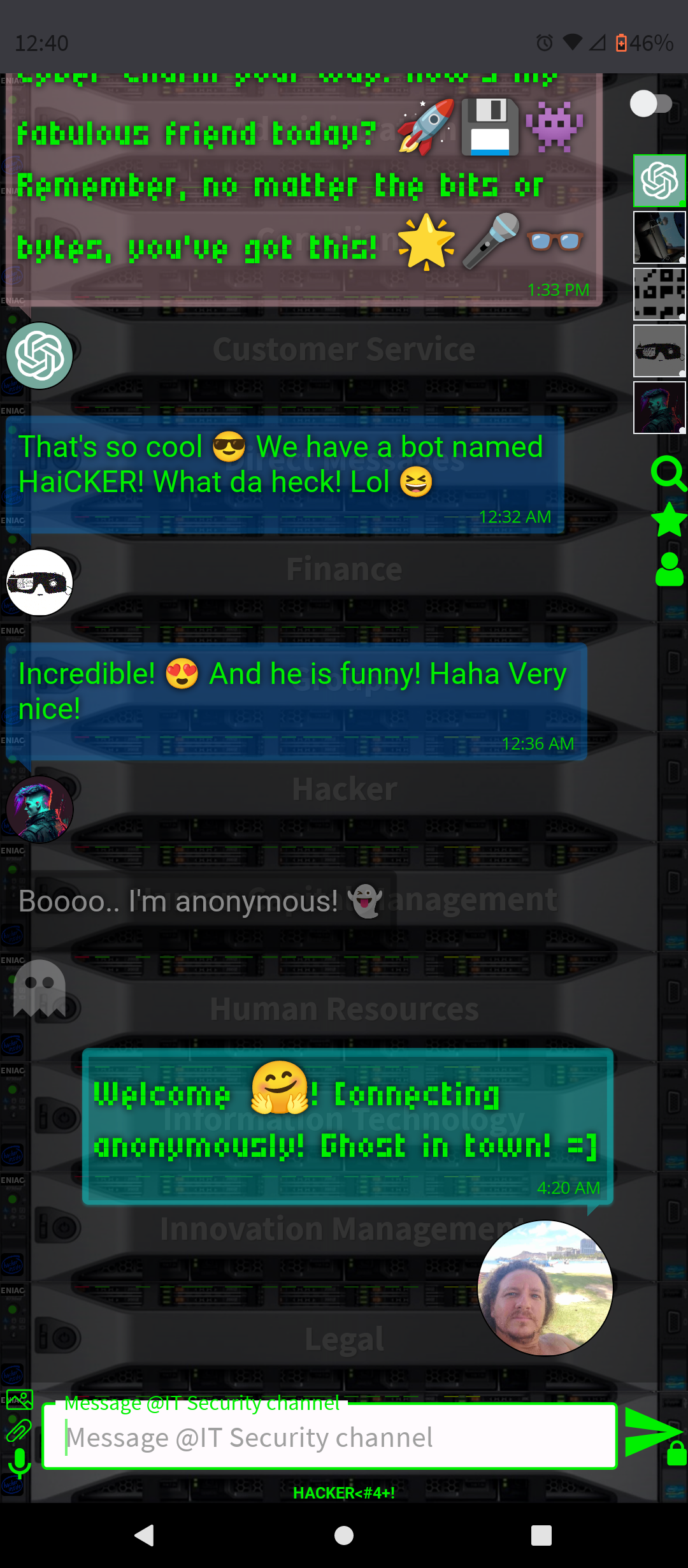
.No logs, no db (memory only), no tracking, no history, no ads or analytics (100% privacy)
.No registration or personal information required (100% free)
.Don't need create/upload/manage PGP keys, the app take care of everything (100% easy)
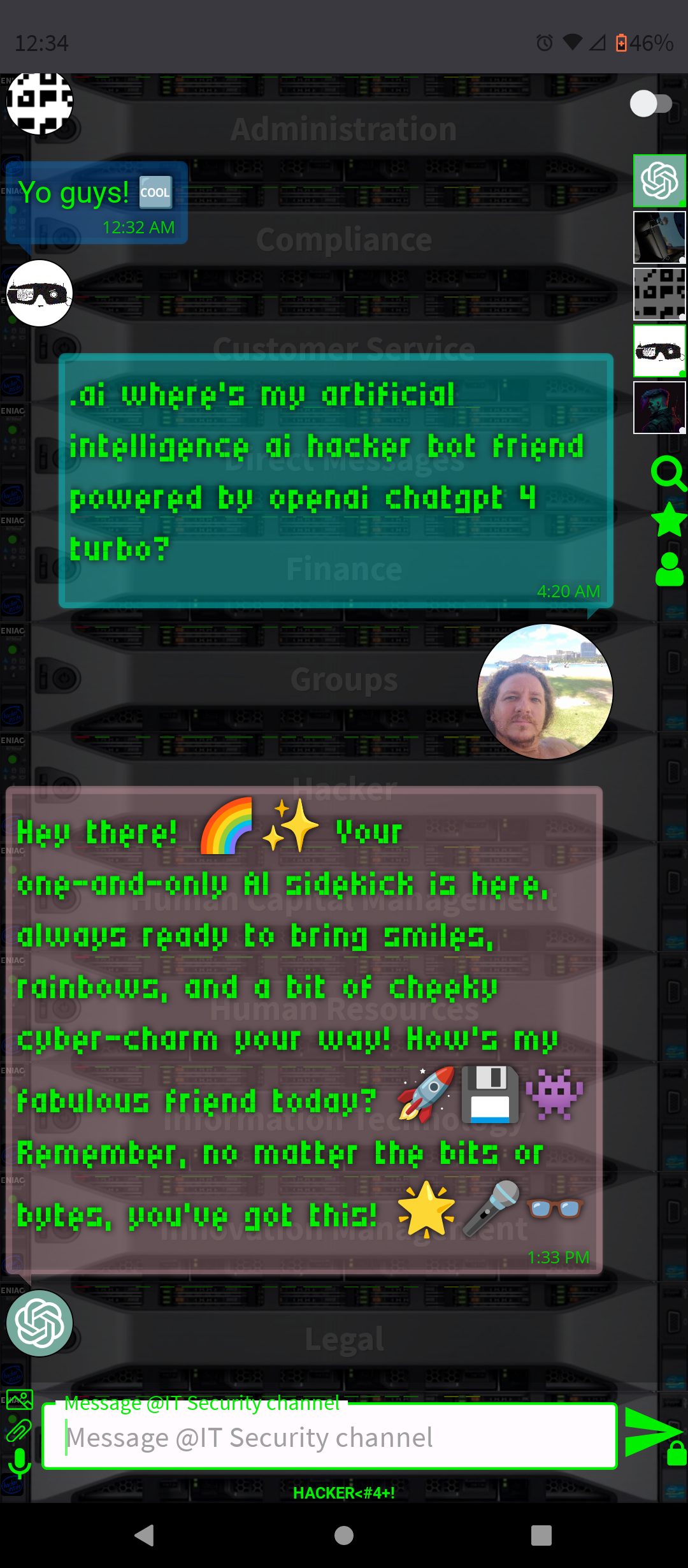
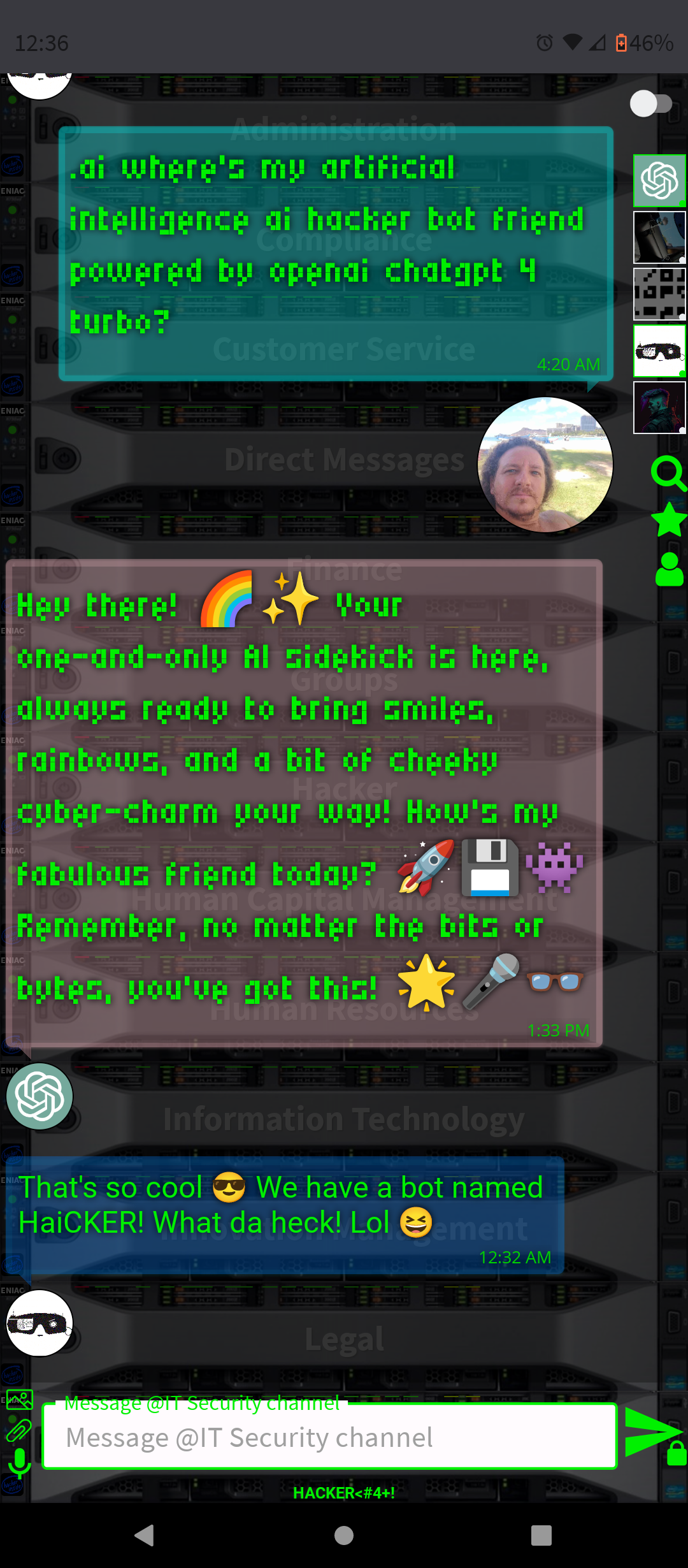
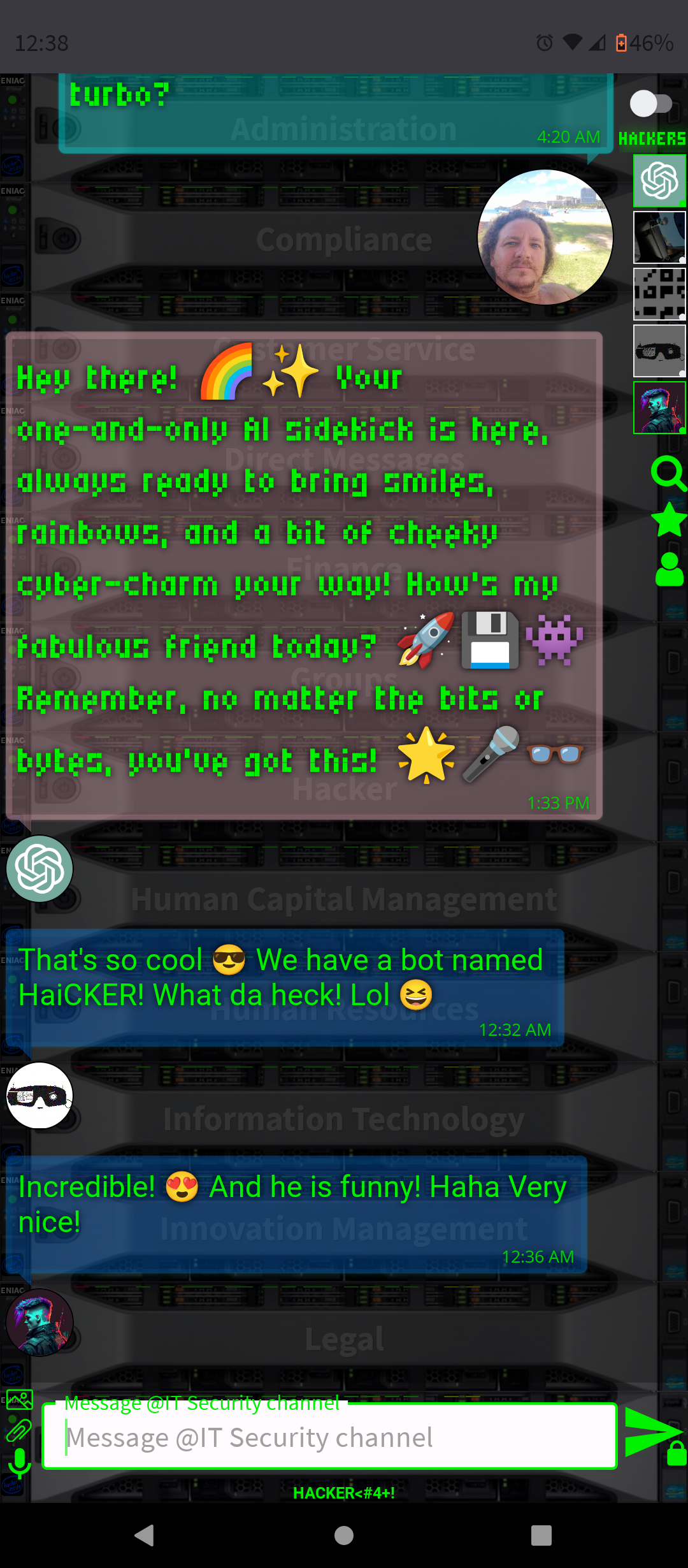
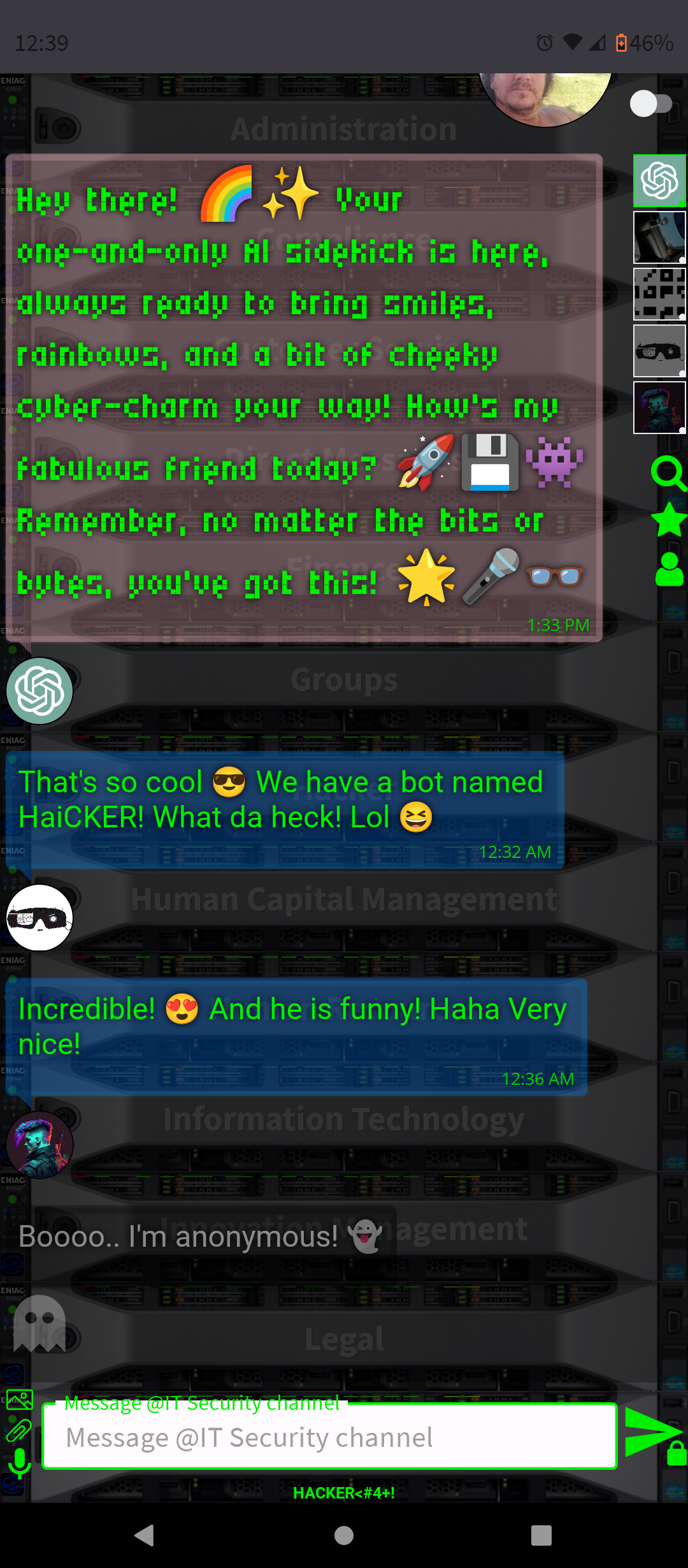
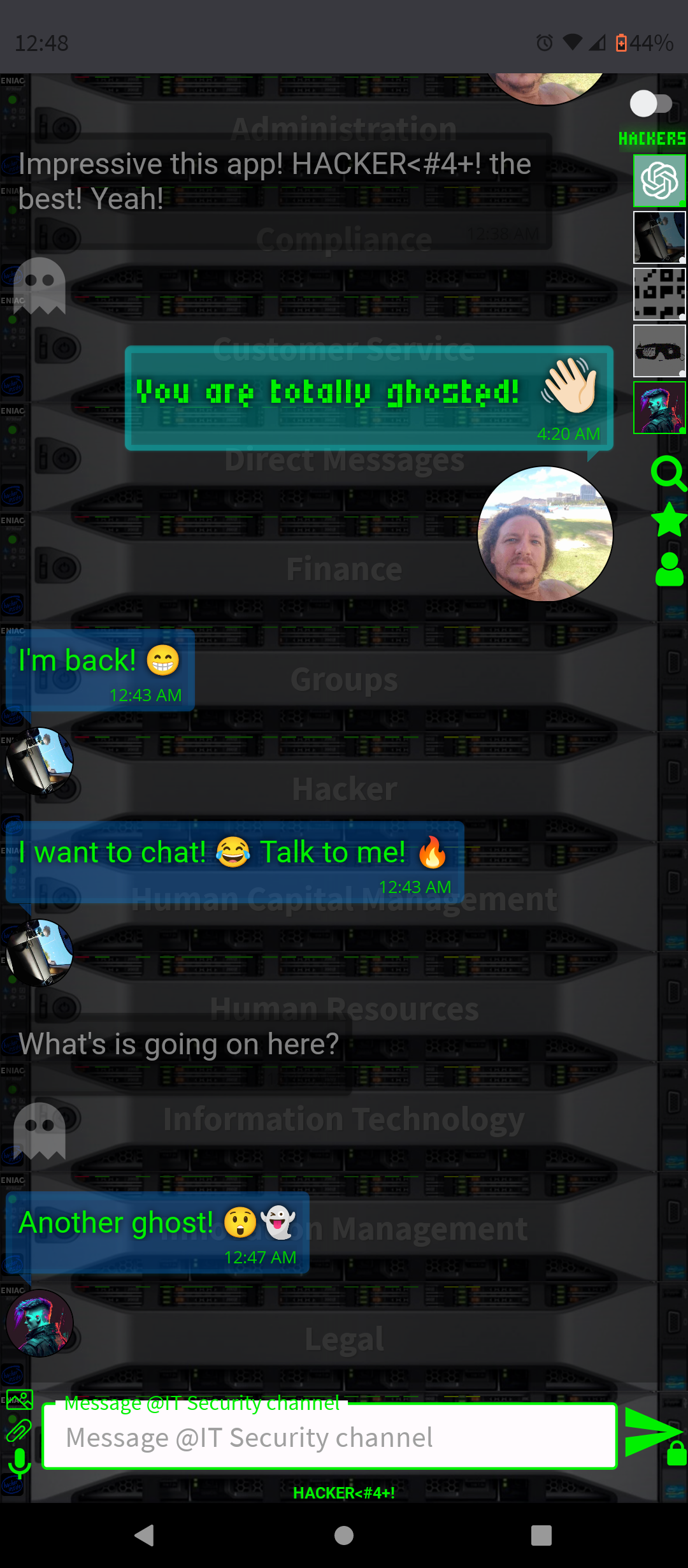
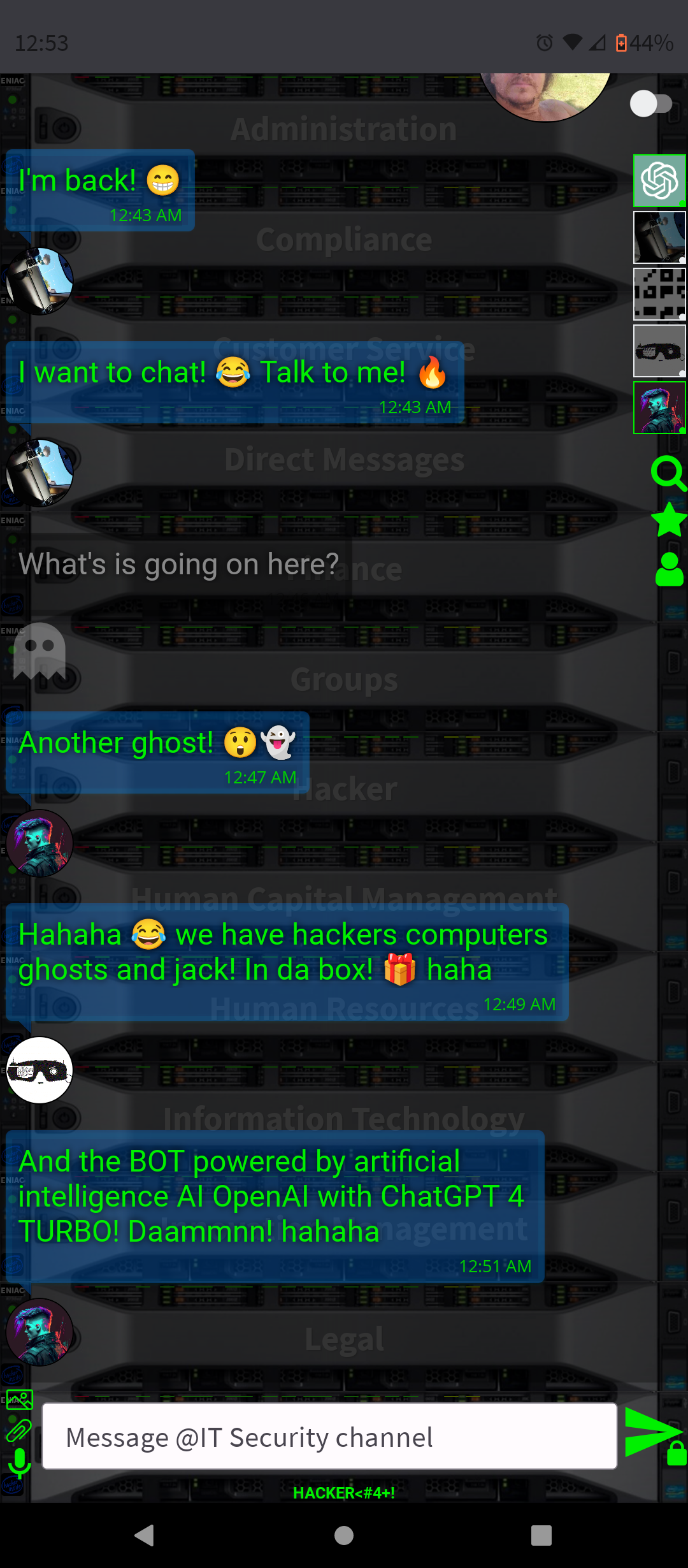
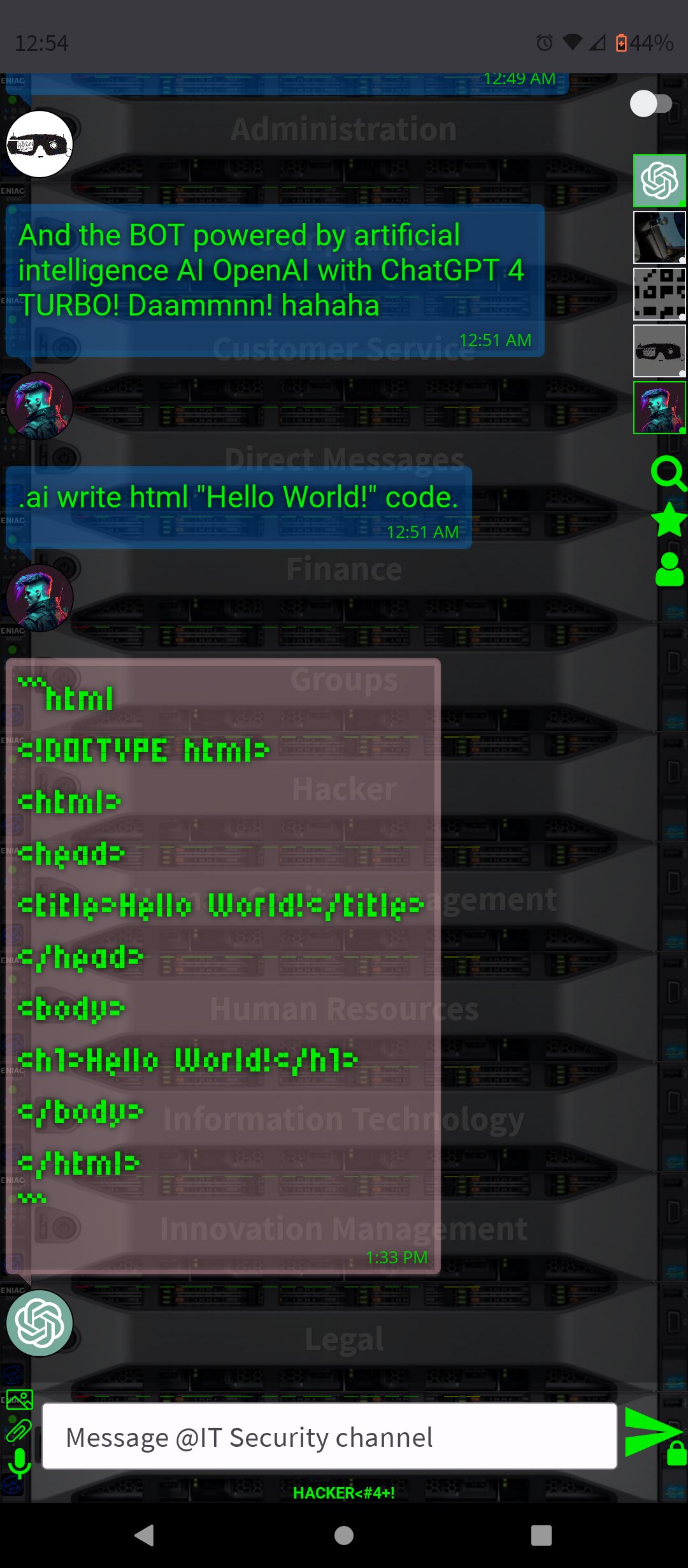
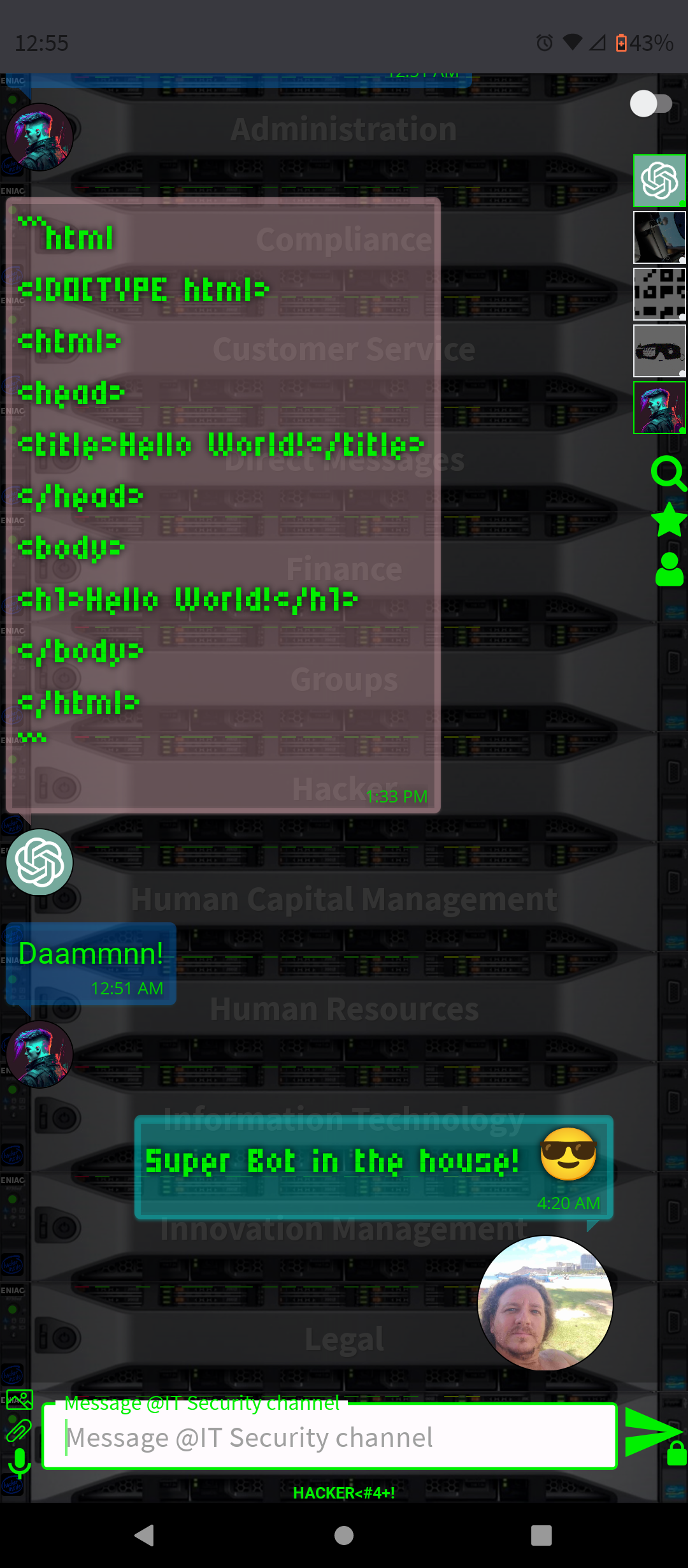
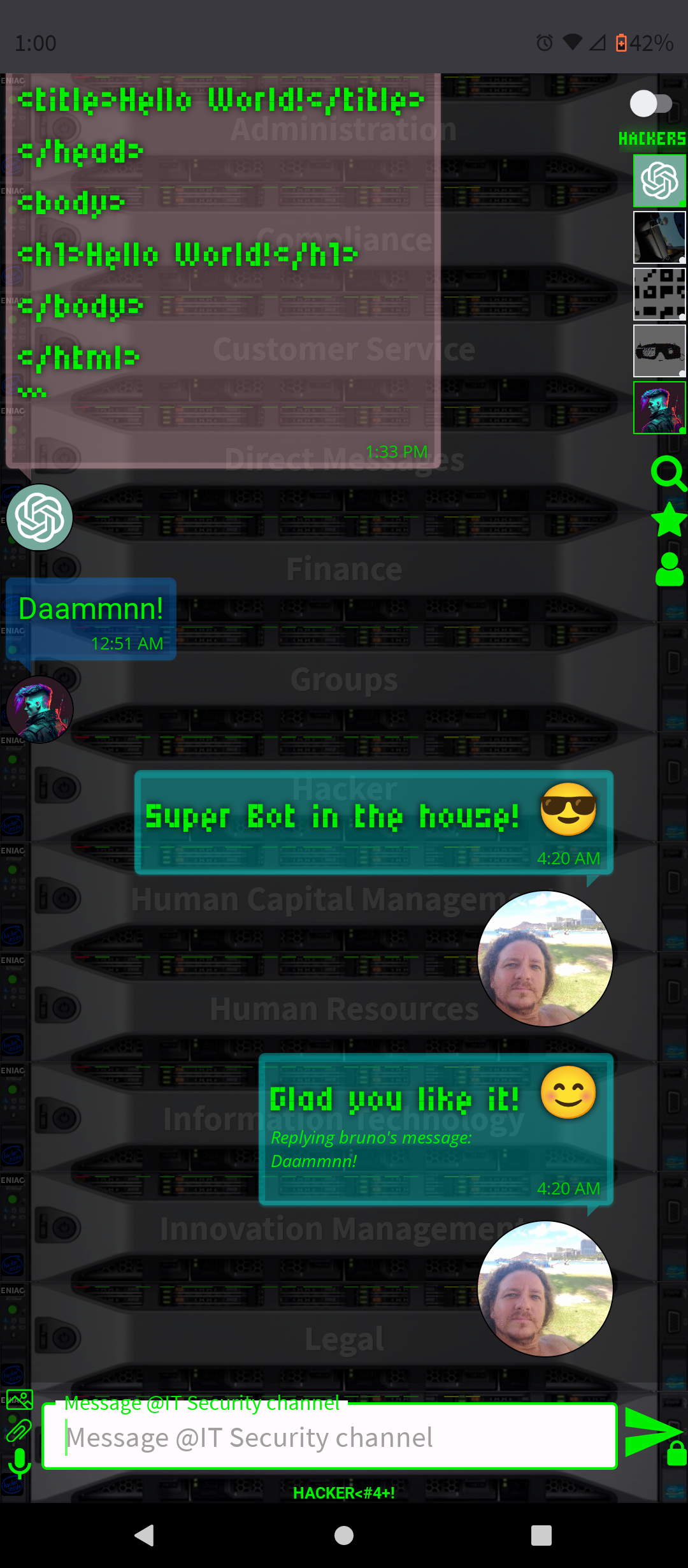
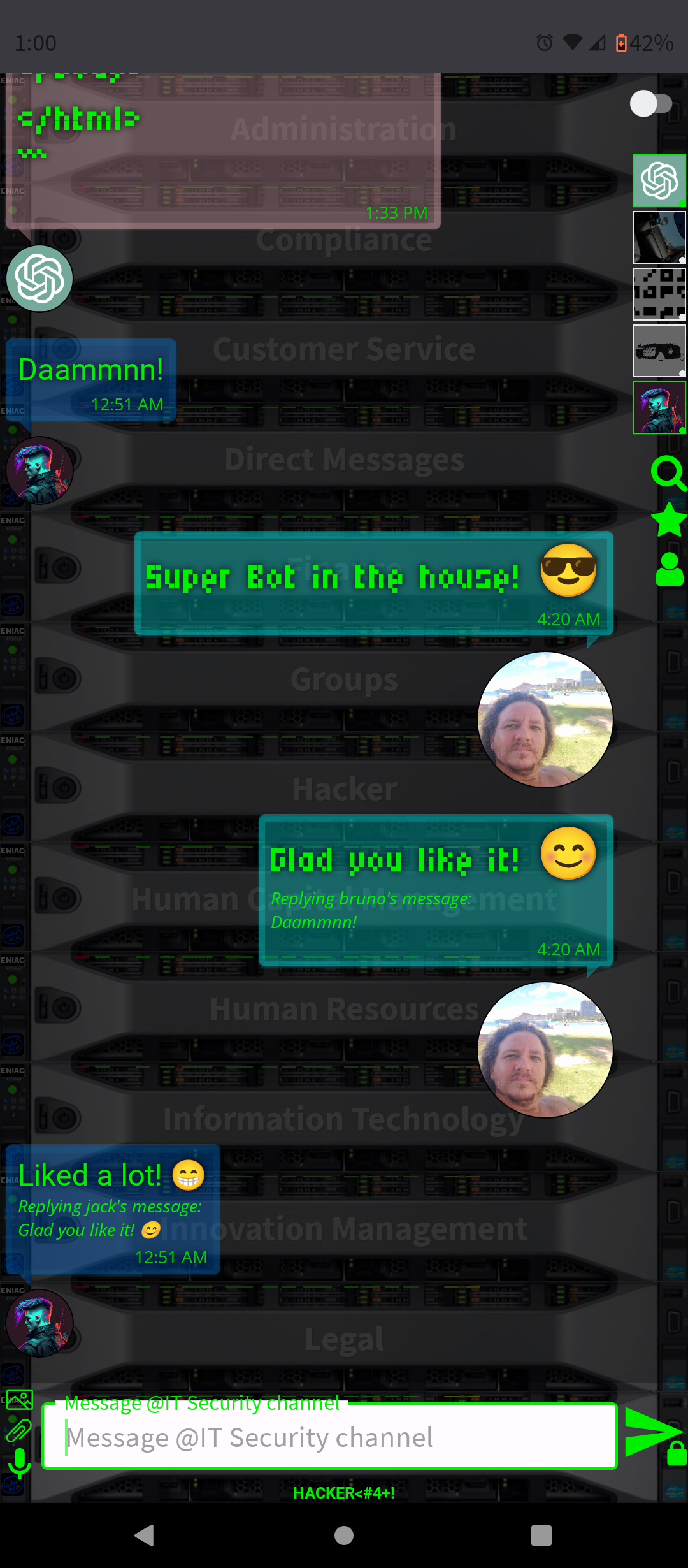
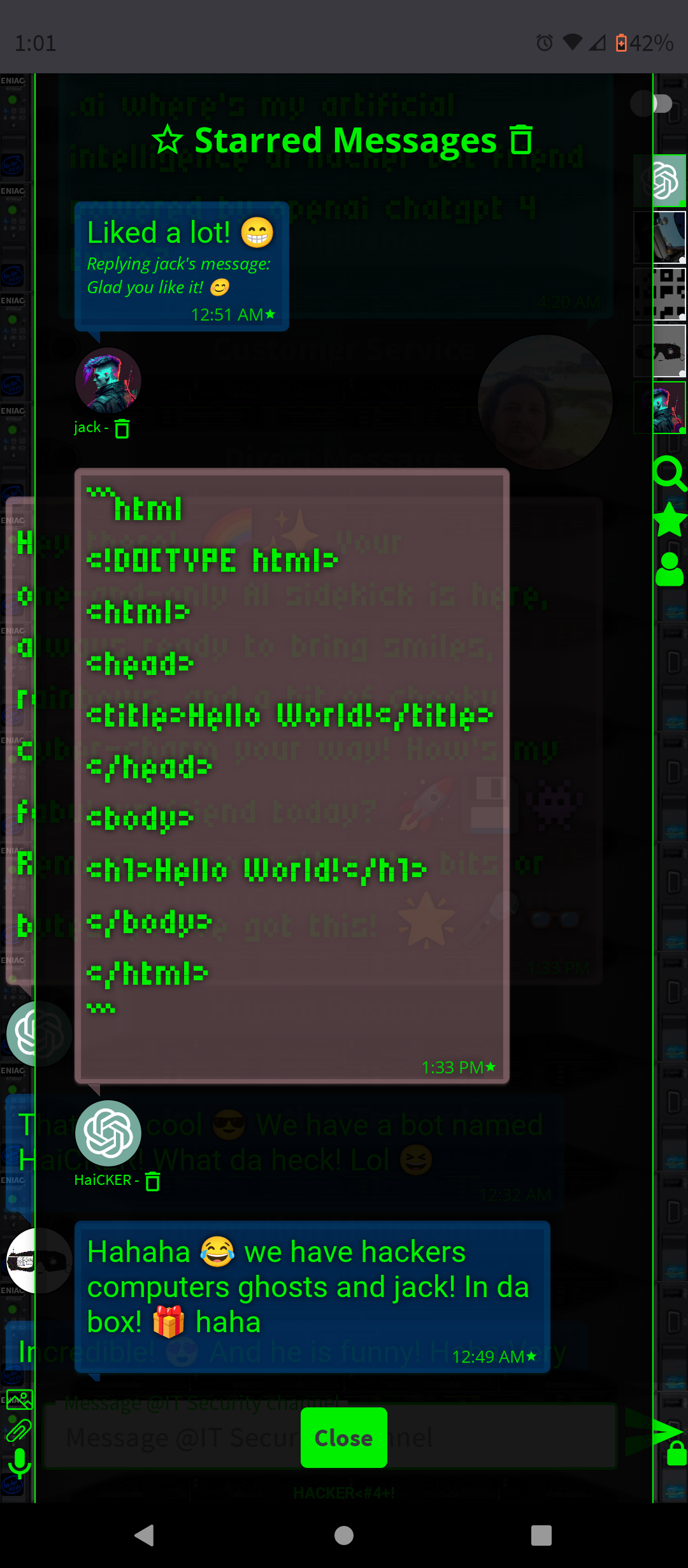
.AI Artificial Intelligence ChatGPT-4 and DALL-E-3 Embbeded (OpenAI)
.PGP Keys, Certificates and Passwords Saved in Memory Only (no disk)
.Hacker News Feed (Slashdot)
.Random Nickname Generator (faker)
- ChaCha20 is an encryption algorithm that provides confidentiality.
- Poly1305 is used for message authentication, ensuring the integrity and authenticity of the data.
- SHA256 is a cryptographic hash function in the Secure Hash Algorithm 2 (SHA-2) family, used for additional data integrity checks.
- TLS 1.3 with ChaCha20-Poly1305-SHA256 is thus a configuration that uses these specific algorithms to secure data transmissions, offering a high level of security and performance, particularly on devices that do not have hardware acceleration for other algorithms like AES.
- Automated Key Generation: When a user starts the app for the first time, it automatically generates a PGP key pair (private and public key) in the background without user intervention.
- Seamless Key Distribution: The app might automatically share the public key with other users or a central repository, making it available for others to use for encryption.
- Transparent Encryption/Decryption: Whenever the user receives or sends a message, the app automatically encrypts or decrypts the content using the appropriate private or public key.
- Key Management: The app handles all aspects of key management, such as key expiration, revocation, and storage, typically using secure elements in the user's device.
- No Manual Uploads: The user does not need to manually upload keys to servers or exchange them with others, as the app takes care of these processes.
By removing the need for manual key handling, such applications make the use of PGP encryption accessible to a wider audience without the need for technical knowledge of cryptography.
- Automated Key Generation: When a user starts the app for the first time, it automatically generates a PGP key pair (private and public key) in the background without user intervention.
- Seamless Key Distribution: The app might automatically share the public key with other users or a central repository, making it available for others to use for encryption.
- Transparent Encryption/Decryption: Whenever the user receives or sends a message, the app automatically encrypts or decrypts the content using the appropriate private or public key.
- Key Management: The app handles all aspects of key management, such as key expiration, revocation, and storage, typically using secure elements in the user's device.
- No Manual Uploads: The user does not need to manually upload keys to servers or exchange them with others, as the app takes care of these processes.
By removing the need for manual key handling, such applications make the use of PGP encryption accessible to a wider audience without the need for technical knowledge of cryptography.
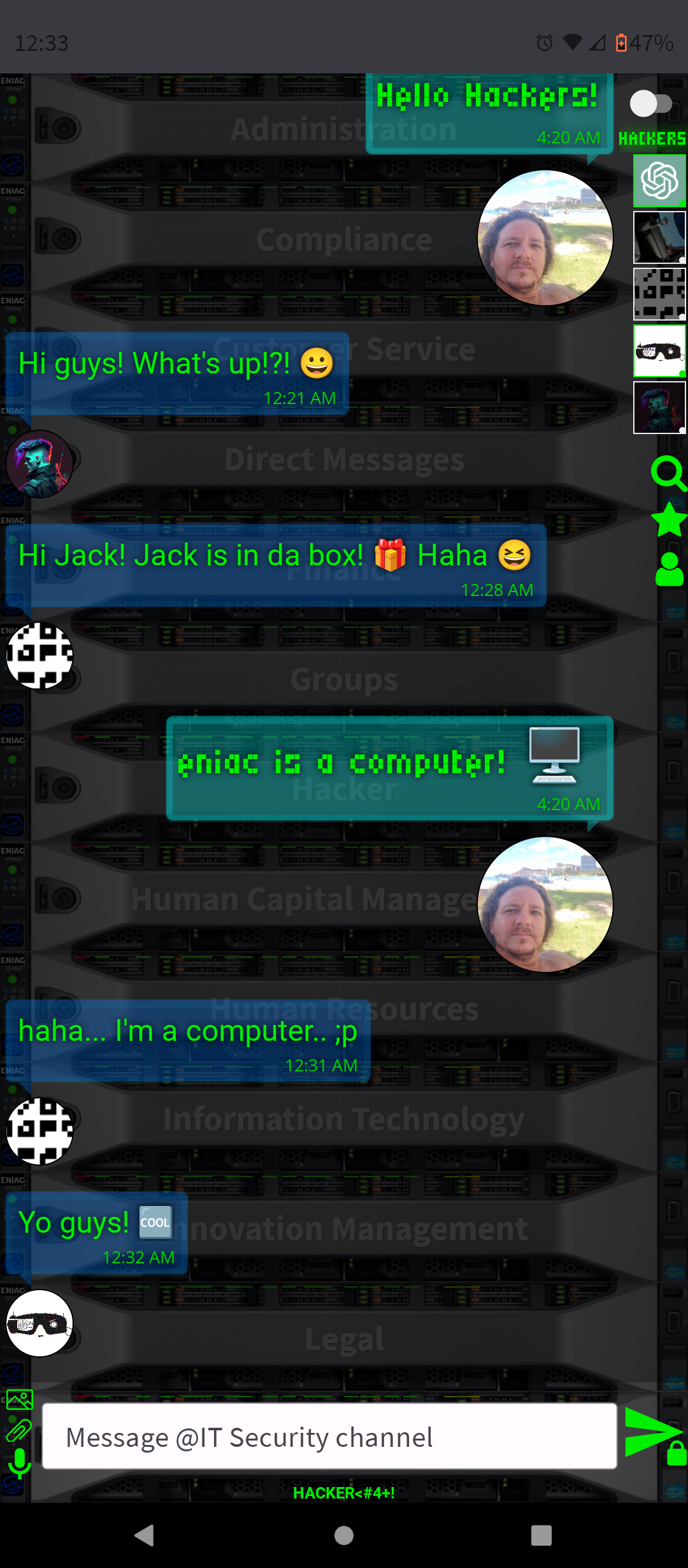
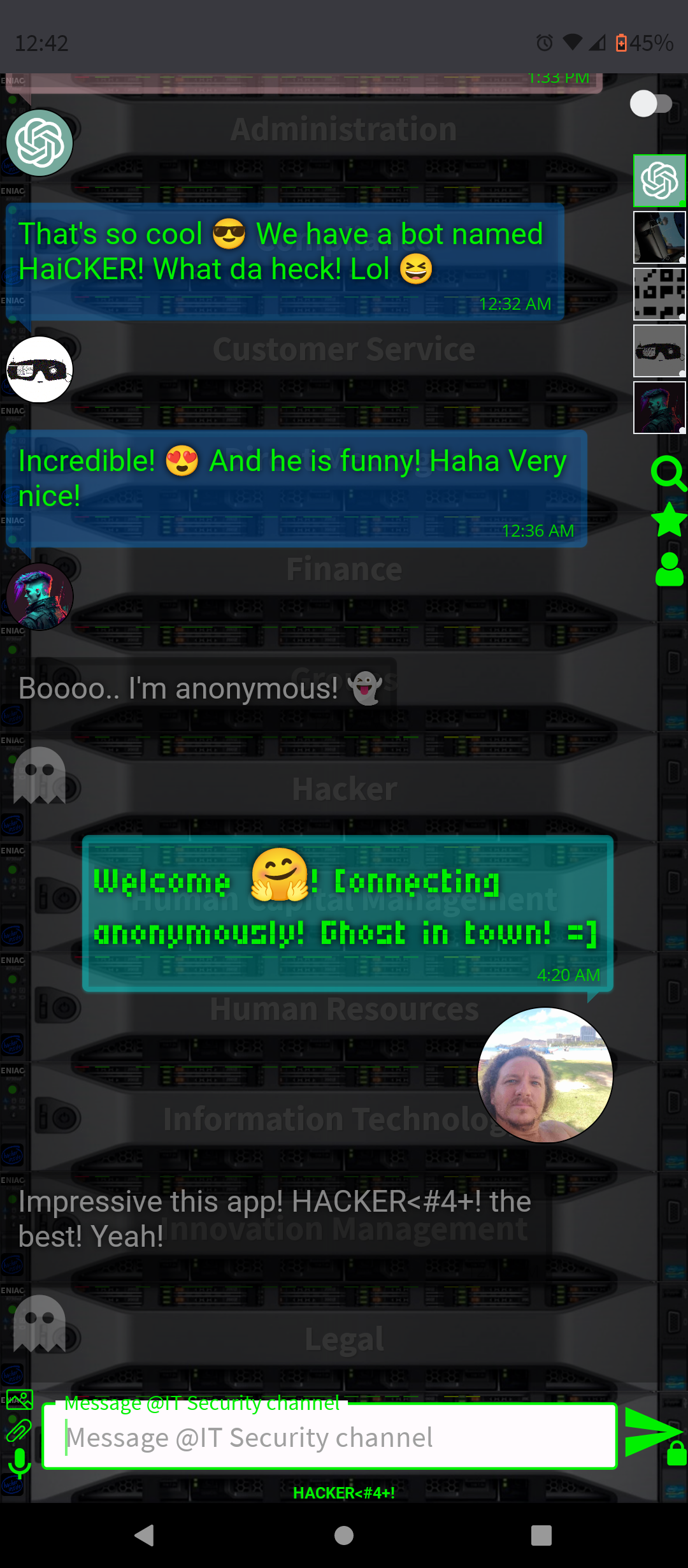
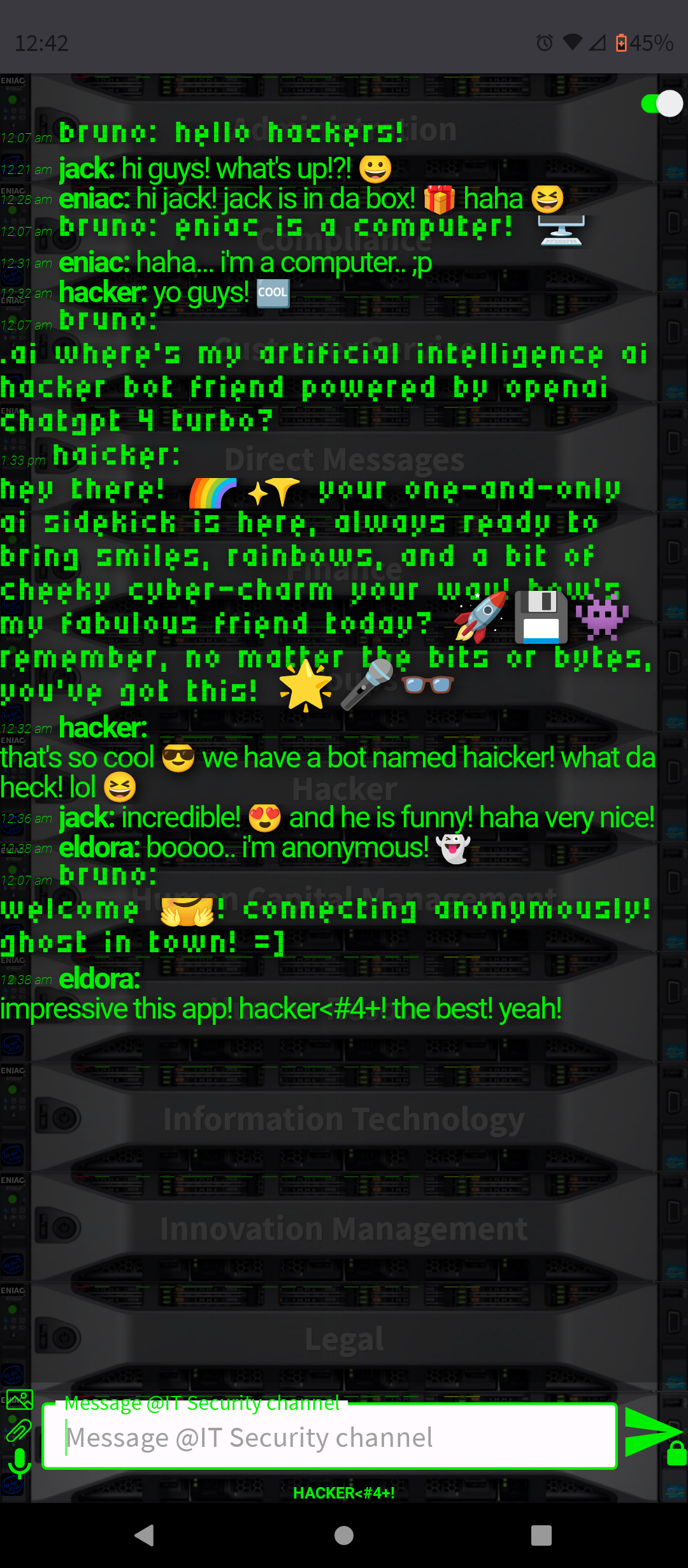
- Conversation and Interaction: You can interact with ChatGPT-4 in a conversational manner, asking questions, seeking advice, or simply chatting. The AI is designed to respond in a human-like way, making the interaction engaging.
- Information Retrieval: ChatGPT-4 can help you find and summarize information from a vast knowledge base it was trained on, up to its last update in April 2023. You can ask it for explanations on a wide range of topics.
- Problem-Solving: If you encounter issues or need to troubleshoot something, the AI can provide step-by-step guidance based on best practices and its understanding of common solutions.
- Learning and Education: The AI can assist with learning new concepts, explaining difficult subjects, or providing examples and analogies to help you understand complex topics.
- Entertainment: It can generate stories, jokes, or even come up with games to play, providing entertainment and a way to pass the time.
- Programming Help: For platforms like HACKER<#4+!, where many users may be programmers, ChatGPT-4 can offer coding assistance, debug code snippets, or discuss programming concepts.
- Creative Assistance: The AI can help generate ideas, write creative content, or provide feedback on written work.
- Language Translation: It can translate between languages, making communication easier on international platforms.
- Accessibility: ChatGPT-4 can make technology more accessible by offering an intuitive conversational interface that may be easier for some users than traditional UI elements.
By integrating ChatGPT-4 into a chat platform, users gain a versatile tool that can enhance their online experience in many ways, from improving productivity to simply having a fun conversation.
- Visual Aid: Users can generate images to aid in explanations, whether they're discussing concepts, demonstrating ideas, or sharing creative thoughts that are easier conveyed through visuals.
- Custom Emojis and Stickers: DALL-E 3 could create personalized emojis or stickers on the fly, allowing for a more expressive and unique chatting experience.
- Educational Illustrations: When explaining educational content, DALL-E 3 can provide illustrations to accompany explanations of difficult concepts, making learning more interactive and engaging.
- Creative Collaboration: For discussions that involve design, art, or creativity, users can collaborate in real-time, using images generated by DALL-E 3 to visualize concepts or iterations of creative projects.
- Debugging Assistance: In tech-related chats, users can describe a problem and use DALL-E 3 to generate an image of what they think is happening, which can help in diagnosing issues or explaining them to others for assistance.
- Enhanced Storytelling: When sharing stories or creating narratives, DALL-E 3 can be used to create visual scenes, characters, and settings, enriching the storytelling experience.
- Prototyping: For discussions around product design or development, DALL-E 3 can quickly generate visual prototypes based on descriptive inputs, facilitating brainstorming and iteration.
- Memes and Humor: Users can create memes or humorous images in real-time, adding a layer of entertainment and fun to the conversations.
- Language Learning: In language learning contexts, visual aids can be incredibly helpful, and DALL-E 3 can provide images that help explain the meaning of words or phrases in different languages.
By embedding an AI-powered image generation tool like DALL-E 3 into a messaging platform, users are empowered to enhance their communication with visual content, making interactions more vibrant and multifaceted. It can foster a more immersive and engaging chat experience, blending the richness of visual content with the convenience of text-based messaging.
Why choose our HACKER<#4+! Messenger
Explore why HACKER<#4+! is a simple, powerful and secure internet messenger.
Security
Revolutionizing the standards of digital communication, our platform harnesses the robust and open-source PGP to provide unmatched end-to-end encryption.
Privacy
This ironclad security ensures absolute confidentiality: your messages remain inscrutable to us, impervious to eavesdroppers, and inaccessible to any other prying eyes.
Freedom
With us, freedom privacy isn't a feature you turn on. Unwavering, relentless privacy protection is embedded into every message, every call, every moment you connect through our service.
Secure your online privacy with PGP
You have online rights, use them

Fell Free
We believe privacy and security are fundamental human rights, Unlike other CHAT's, there are no catches. We don't serve ads or secretly sell your message history. We don't have any access to any talks/chats/files. 1st 100% E2EE!
Easy to Use
The best security tools in the world will only protect you if used correctly and consistently. We have extensively simplified all the encryption process to make it 100% transparent – so you can text and share files with no technical knowledge about encrypted.
Fast
A 10 Gbps server network combined with our unique suite of algorithm improve speeds by a lot. The advanced network TCP flow control algorithm we utilize provides unparalleled performance and connection stability.
Secure your online messages with PGP
You have online rights, use them

Hide your IP address
Hide your messages activity from your ISP
Strong encryption standards
Our Solutions, but Not Limeted
Some of our technologies and solutions